How MSPs can enable remote collaboration for customers without jeopardising security
As COVID continues to loom large, companies from all around the world see no end in sight to the rise in virtual work and remote operations.
Remote-working collaboration tools have become a lifeline for businesses and their employees in their bid to stay connected and productive. Everyone from small businesses to corporate giants has been busy adopting cloud-based solutions.
This mass migration of data into the cloud, though, makes organisations much more vulnerable to ransomware attacks and other types of hacks.
The biggest challenge for security teams is the risk of losing visibility and control over how sensitive data is being managed and protected. Security should never be sacrificed as a trade-off for convenience and speed.
Cloud security challenges
As work has become more flexible, so have the ways in which we communicate and collaborate. Microsoft 365 and Google Workspace were already the productivity suites of choice for millions, but other software-as-a-service (SaaS) has also grown in popularity over the last 18 months, such as Salesforce.
However, the growth of cloud communication and collaboration amplifies the challenge of keeping sensitive data secure as it moves freely between the cloud and users, bypassing any perimeter-based security measures.
Managed service providers face a serious challenge as people switch between working from home, in coffee shops, the office or wherever they find themselves in transit.
When customers have employees working from multiple locations and using a mix of work issued and personally owned devices, how is it possible for MSPs to manage and protect the data that staff access and transfer?
How do MSPs protect their customers from data compromise and loss? And how do they do that without hindering the productivity of employees and giving the impression that there is a lack of trust in the staff?
The importance of strong user access management
As an MSP there will be times when you want to safely allow customers to back up or manage their own data, or securely provide them with more visibility as part of their managed service.
With the right processes and technology in place it is possible for administrators to customise granular permissions for customers and products, depending on access needs.
Are you able to manage and protect customer data within a single interface? And can you customise and control who has access to customer data?
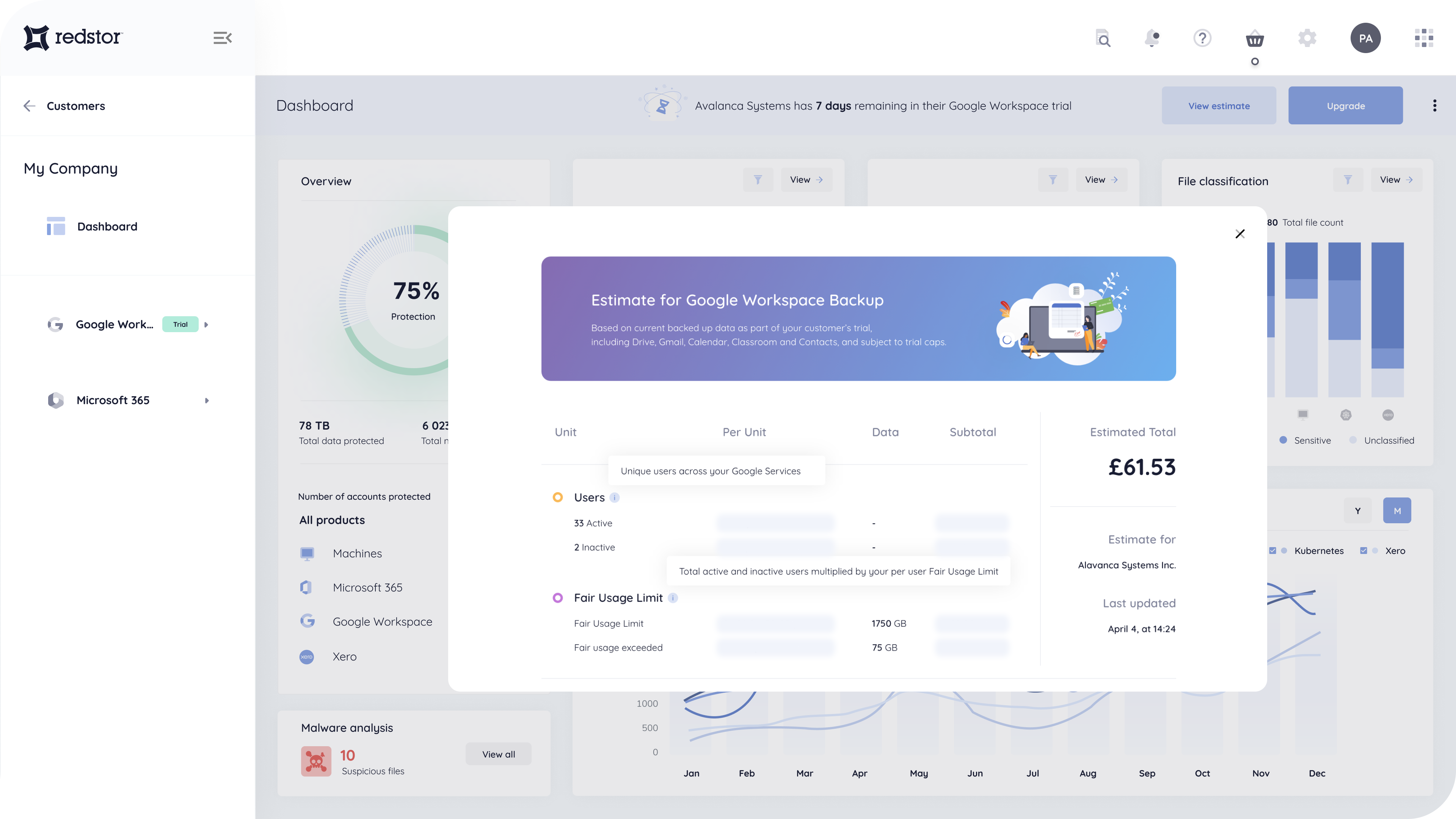
Find out more about Redstor’s smart data management and protection
Secured by the very latest multi-factor authentication technology, Redstor enables you to manage and protect a multitude of data environments . . . within a few clicks.
Redstor offers the broadest coverage of support, spanning modern and legacy data infrastructure and an ever-widening array of SaaS applications and platforms, including Microsoft 365, Google Workspace, Salesforce and Xero, with no hardware requirements – through a single app.
With Redstor you can reduce overheads by managing all company sites and remote user devices through a single, intuitive, cloud-native app that scales effortlessly.
In the event of an issue, you can intelligently prioritise recoveries and allow users to access data in seconds whilst the full recovery continues in the background, as well as migrate data across different cloud and infrastructure environments, seemingly instantly, using InstantData™, a pioneering new technology.
- Set up strong security
Protect against data breaches, identity theft and forbidden access to confidential information. Prohibit the spread of compromised login credentials. Block unauthorised entry to a network. Bolster defences against ransomware, hacking, phishing, and other cyber-attacks. - Customise roles
Assign specific users to products, customers or group of customers within an estate. Customise permissions and notifications within the product – such as deleting data, recovering data, receiving alerts about suspicious files and creating and managing other users and customers - Streamline IT workloads
Update a security policy easily and comprehensively. Change all access privileges across an organisation in one action and save IT time by automating more tedious tasks e.g. password reset requests. - Comply with regulations
Quickly implement Identity Access Management best practices for customers to meet the requirements of their industry regulations e.g. Health Insurance Portability and Accountability Act and General Data Protection Regulation. - Enable customers to collaborate securely with third parties
Help your customers improve productivity by enabling them to give their clients, suppliers, and visitors access to their network whenever they wish – without jeopardising security.