Cloud-first backup with zero hardware
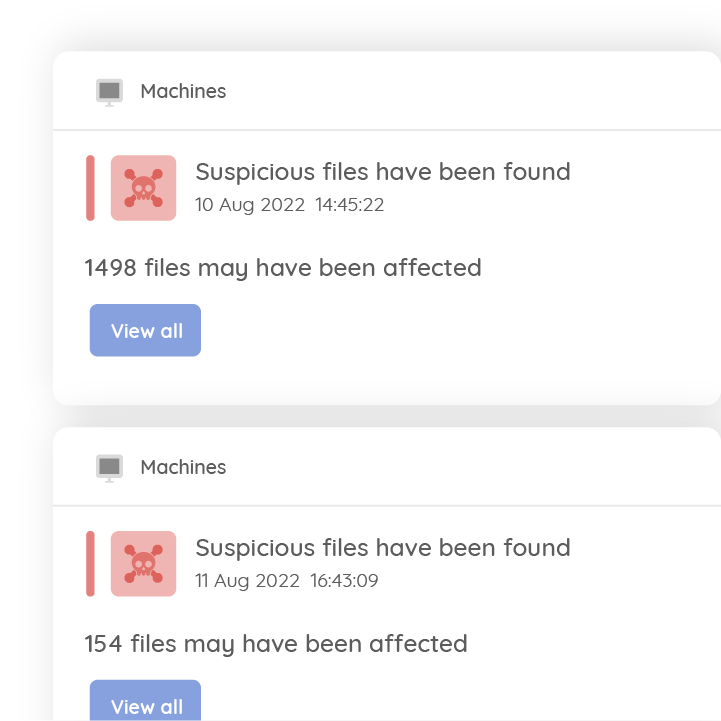
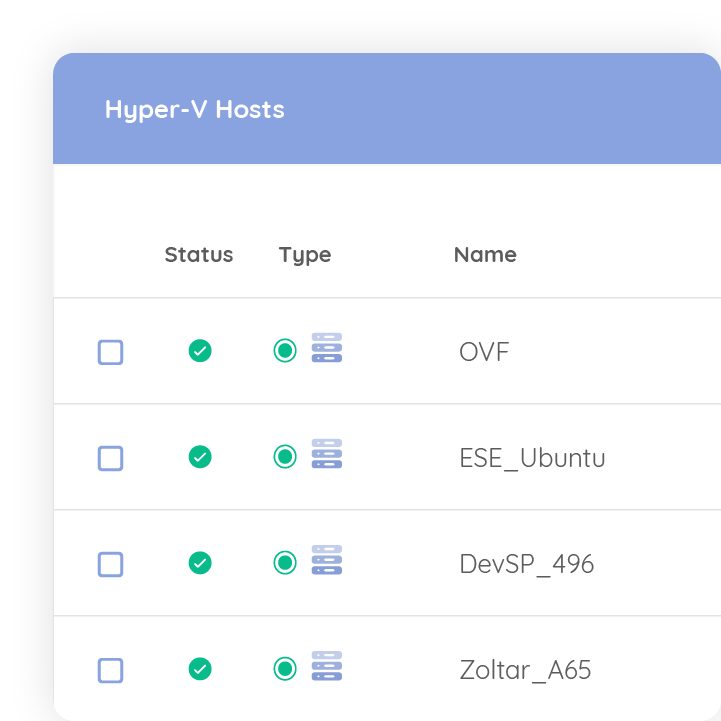
Back up your systems to the cloud and recover them to a different physical machine or a Hyper-V or VMware virtual machine. Choose between restoring the whole system, the system state, or just bare metal. With Redstor, your data is backed up to two cloud locations, with an optional local copy available free of charge.