Smarter backup
technology
Smarter cloud data backup, with zero hardware required, delivering the broadest coverage of data sources from a single app and lightning-quick recovery of any files on demand.
MSPs
Purpose-built for service provision, designed for MSPs that want to outperform the market
End Users
Discover, manage and protect your data in the simplest, smartest, safest way, with recovery of any file, in an instant
Smarter cloud data backup, with zero hardware required, delivering the broadest coverage of data sources from a single app and lightning-quick recovery of any files on demand.
Smarter cloud data backup, with zero hardware required, delivering the broadest coverage of data sources from a single app and lightning-quick recovery of any files on demand.
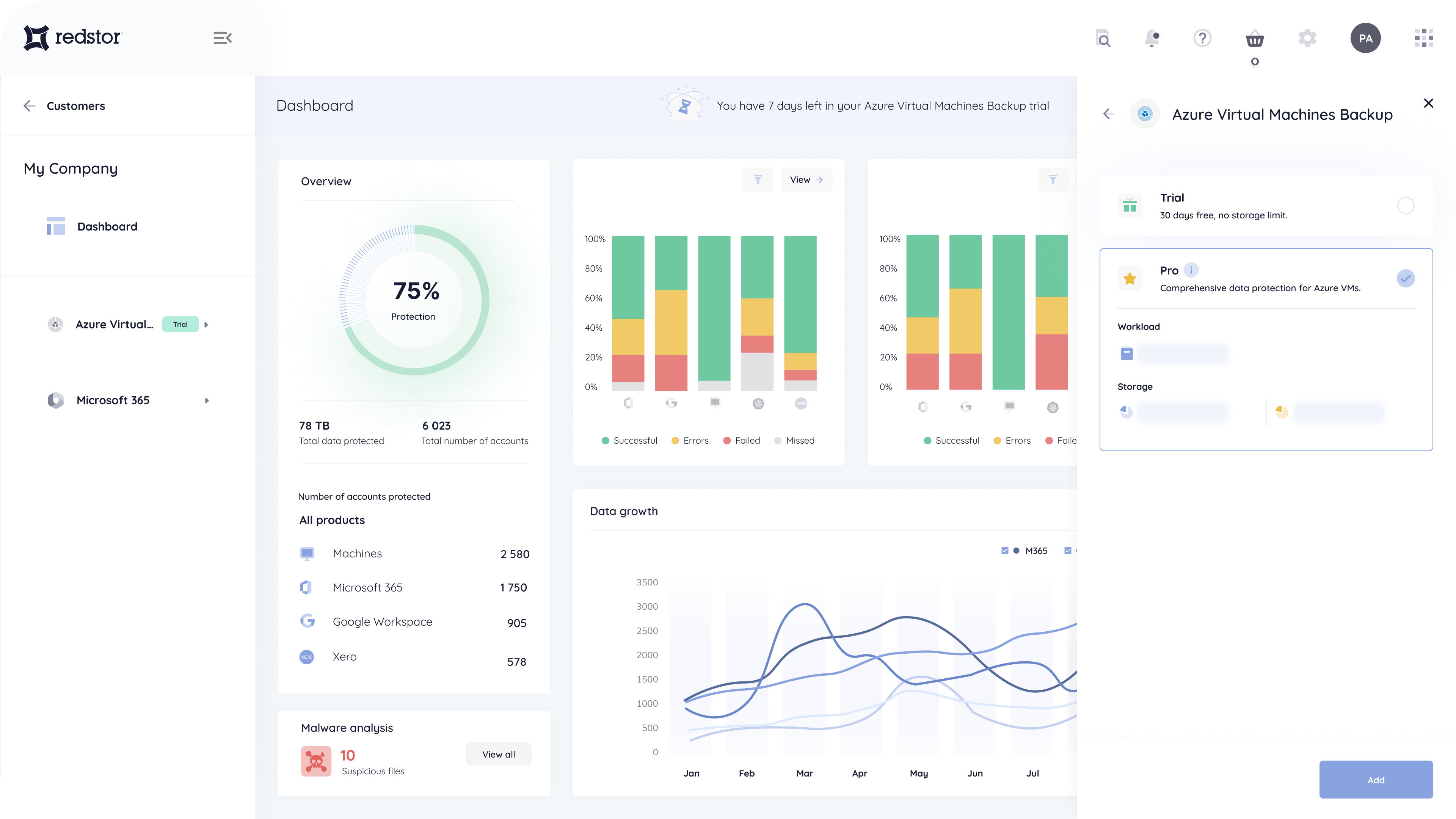
The RedApp is Redstor’s web-based command center. This intuitive, multi-tenant app, incorporates backup, archiving and recovery services supporting infrastructure, cloud-native environments and an ever-widening array of SaaS Apps as well as data migration from, to and between cloud platforms.
The RedApp is Redstor’s web-based command center. This intuitive, multi-tenant app, incorporates backup, archiving and recovery services supporting infrastructure, cloud-native environments and an ever-widening array of SaaS Apps as well as data migration from, to and between cloud platforms.
Traditional recovery methods require waiting for all data to be restored completely before files are accessible. This challenge is exacerbated when recovering over the Internet. InstantData™’s innovative technology overcomes this, providing immediate access to your backed-up files either on a temporary basis or during a DR scenario.
Traditional recovery methods require waiting for all data to be restored completely before files are accessible. This challenge is exacerbated when recovering over the Internet. InstantData™’s innovative technology overcomes this, providing immediate access to your backed-up files either on a temporary basis or during a DR scenario.
Malware Detection uses machine learning to protect every customer’s data from files containing malware, quarantining files believed to be malicious and allowing the user to then either mark them as safe or remove the files and revert to a previous, safe version.
Since launch in 2021, zero customers that have enabled malware detection have experienced infected recoveries.
Malware Detection uses machine learning to protect every customer’s data from files containing malware, quarantining files believed to be malicious and allowing the user to then either mark them as safe or remove the files and revert to a previous, safe version.
Since launch in 2021, zero customers that have enabled malware detection have experienced infected recoveries.
Data tagging utilises AI to identify which backed up data should be classed as highly sensitive or sensitive, allowing better data risk management. For example, it may identify that 90% of an organisation’s most sensitive files are stored on a single machine, or that 75% of data held within a Google Workspace user’s account is highly sensitive.
Data tagging utilises AI to identify which backed up data should be classed as highly sensitive or sensitive, allowing better data risk management. For example, it may identify that 90% of an organisation’s most sensitive files are stored on a single machine, or that 75% of data held within a Google Workspace user’s account is highly sensitive.
Redstor’s cloud-native and cloud-first design avoids any need for local hardware, eliminating hardware purchasing, shipping and configuration delays. Similarly, Redstor’s commitment to making backup simpler, safer and smarter has resulted in an intuitive app (RedApp) that doesn’t require extensive training to use.
These advantages mean that data can be protected on day 1.
Redstor’s cloud-native and cloud-first design avoids any need for local hardware, eliminating hardware purchasing, shipping and configuration delays. Similarly, Redstor’s commitment to making backup simpler, safer and smarter has resulted in an intuitive app (RedApp) that doesn’t require extensive training to use.
These advantages mean that data can be protected on day 1.
Redstor’s Archiving service saves disk space by removing redundant, obsolete and trivial (ROT) data.
Redstor’s Archiving service saves disk space by removing redundant, obsolete and trivial (ROT) data.
With support for a wide range of environments including infrastructure, cloud-native and an ever-increasing array of SaaS business apps, Redstor enables centrally and consistently backing up data regardless of where it resides.
Redstor’s unique InstantData™ technology meanwhile, facilitates migrating data between platforms quickly and easily, with minimal downtime, whilst also enabling the provision of temporary, streamed access to SaaS or cloud-based data, in the event of platform downtime.
With support for a wide range of environments including infrastructure, cloud-native and an ever-increasing array of SaaS business apps, Redstor enables centrally and consistently backing up data regardless of where it resides.
Redstor’s unique InstantData™ technology meanwhile, facilitates migrating data between platforms quickly and easily, with minimal downtime, whilst also enabling the provision of temporary, streamed access to SaaS or cloud-based data, in the event of platform downtime.
Redstor’s app enables includes powerful and configurable user and access management (UAM), enabling administrators to create and configure users with highly customizable access and permissions depending upon the user’s access needs.
RedApp also facilitates locking down functionality for users if required, including quickly and easily managing or completely disabling users in the event that a login is compromised.
Redstor’s app enables includes powerful and configurable user and access management (UAM), enabling administrators to create and configure users with highly customizable access and permissions depending upon the user’s access needs.
RedApp also facilitates locking down functionality for users if required, including quickly and easily managing or completely disabling users in the event that a login is compromised.
Redstor uses Transport Layer Security (TLS ) SSL and AES-256 encryption to ensure the safety of all data it protects, along with role-based permissions and 2FA on the app. Users create and manage their encryption keys, meaning that only they can decrypt and recover their data.
Redstor uses Transport Layer Security (TLS ) SSL and AES-256 encryption to ensure the safety of all data it protects, along with role-based permissions and 2FA on the app. Users create and manage their encryption keys, meaning that only they can decrypt and recover their data.
7 min
1 min